You may install the proxy anywhere in your neighborhood atmosphere. Open Proxies are Proxy Servers that were left open to the general public. Generally, the proxy ought to have the identical up time requirements as your application approach. Nobody can inform you if that proxy you're using is monitored or not. When you're using the Cloud SQL Proxy in a manufacturing environment, there are a few actions you may take to be sure that the proxy stipulates the essential availability for your application.
The Tried and True Method for Proxy Database in Step by Step Detail
Proxy bouncing can be employed to keep up your privacy. Proxies may also be combined with firewalls. The proxy will initially rewrite all the links in that document so that they'll point back to the proxy rather than the internet server. Be sure you get the proxy that satisfies your requirements. It's essential to note that not all the proxies share exactly the same feature collection. Moreover the proxy cannot be detected by the customer computer. A translation proxy is a proxy server which is used to localize a web site experience for unique markets. To learn more about vpn database, visit on hyperlinked site.
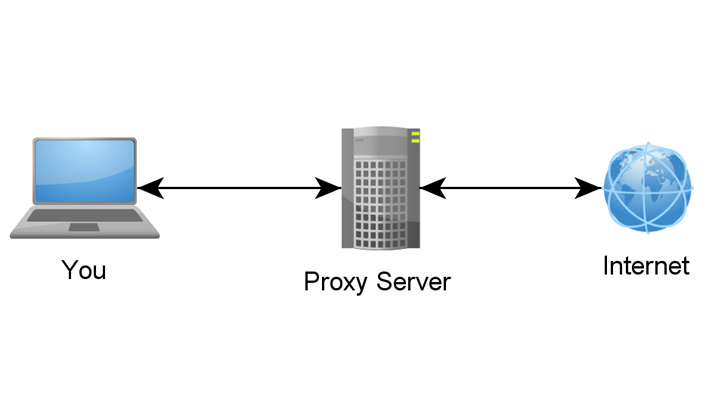
There are many ways to tell the proxy which instances that you want to connect to. A proxy isn't necessary, but it's sometimes convenient. Unfortunately, if it cannot read the MySQL protocol, it cannot distinguish SELECTs from other queries. There might be other forms of programs made to conceal your true identity and specific location but Hide My Ass proxy is distinct in such a way that you don't need to install another software application in order for it to function. The Hide My Ass proxy, for example, is quite remarkable in providing you the privacy and liberty which you would like and prefer. It's possible that XMyIP proxy test doesn't detect some proxies. Firstly, higher anonymity proxies (elite proxies) don't utilize HTTP headers.
As a computer user or network systems administrator, it is critical you know different forms of servers available so the suitable application can be used. In the event the remote server doesn't define a user that's the very same as the user ID you're conneted to the sample database with, you must make an external login for your existing user.
No comments:
Post a Comment